-
Industrial Cyber Security
Providing professional security in an insecure world.

-
Industrial Cyber Security
Right Solution for Right Security. insecure world.

-
Industrial Cyber Security
Right Protection, Right Time.

Leveraging your most powerful intelligence tool
Industrial Cyber security protects the data and integrity of computing assets belonging to or connecting to an organization's network. Its purpose is to defend those assets against all threat actors throughout the entire life cycle of a cyber attack.
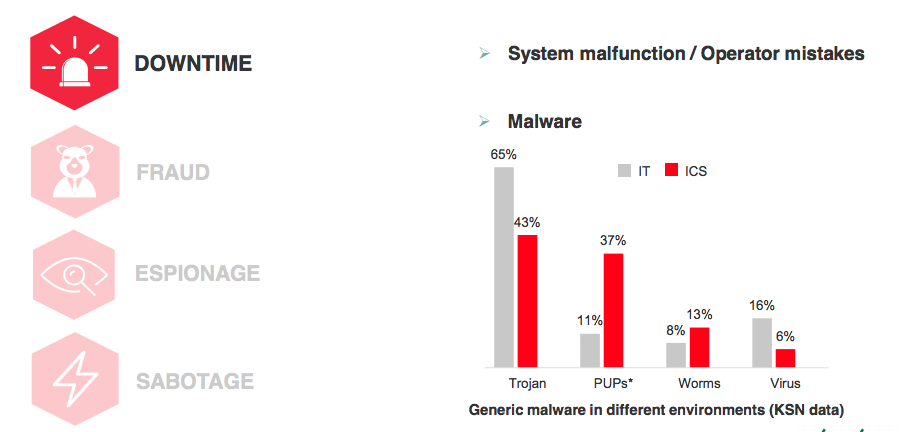
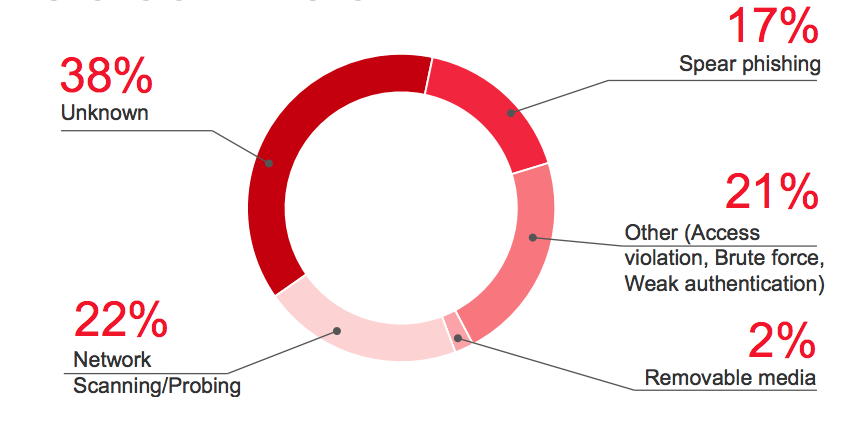
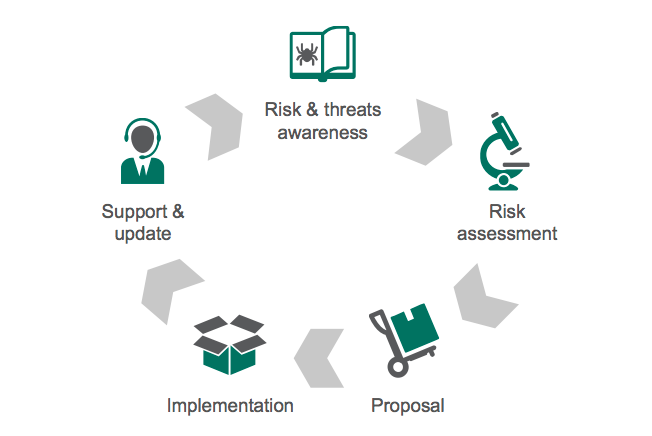
| Threats and Risks factors | KL Technologies to address |
| Appearance of unauthorized network devices at industrial network | Network Integrity Control detects new / unknown devices |
| Appearance of unauthorized communications at industrial network | Network Integrity Control communications between known devices |
Malicious PLC commands by:
|
Monitoring of communications to and from PLCs and control of commands and parameter values of tech process; |
| Lack of data for operators on cybersecurity incidents | Alerts on suspicious tech process parameter changes and malicious to operator (via HMI integration) |
| Lack of data for investigation and forensics | Forensics tools: monitoring and safe logging of industrial network events |
Cybersecurity and awareness trainings,Intelligence (threat feeds and reports),Industrial simulations (e.g. KIPS)
CyberSecurity Assessment (CSA) incl. PenTesting, Solution maintenance, Incident response